AI-Powered Cybersecurity Solutions
overview
As a global IT & ITES partner, Infinite combines domain expertise, industry-aligned frameworks, and advanced automation to deliver secure-by-design solutions across cloud, data, and infrastructure. Our cybersecurity practice helps enterprises protect critical assets, maintain compliance, and build resilience against modern threats – whether on-prem, hybrid, or cloud-native.
Infinite’s cybersecurity offerings are grounded in the NIST Cybersecurity Framework and powered by a 24/7 Security Operations Center (SOC). We enable proactive protection, rapid incident response, and continuous improvement, backed by deep experience across industries such as healthcare, BFSI, and manufacturing.
Our Offerings
Infinite’s Managed SOC provides end-to-end threat monitoring, detection, and response across your enterprise IT landscape. Our AI-powered SOC combines security analytics, threat intelligence, and automation to reduce dwell time and contain threats before they escalate.
Key capabilities include:
- 24/7 monitoring and incident response
- Integration with SIEM, EDR, UEBA, and SOAR
- Cloud-native and hybrid SOC delivery models
- Threat hunting, forensic investigation & compliance reporting
- SOC maturity assessments aligned with NIST
- Gold teaming, red/blue team simulations, and playbook-driven response
Infinite helps organizations streamline identity lifecycle management across cloud and enterprise systems. From zero-trust-based access controls to federated authentication, our IAM services ensure secure, frictionless access for users at scale.
- Role-based (RBAC) and attribute-based (ABAC) access models
- Multi-factor authentication (MFA), SSO, PAM
- Identity Governance & Lifecycle automation
- Directory services (Active Directory, Entra ID)
- Identity analytics, behavior monitoring, and compliance reporting
- ICAM (Identity, Credential, and Access Management) frameworks
Identify and fix weaknesses before attackers exploit them. Infinite’s continuous vulnerability management service prioritizes real risks and remediates them effectively – leveraging your existing tools or ours.
- Risk-based scanning & assessment
- Penetration testing (black/white box)
- Cloud, network, application, and endpoint coverage
- OSINT and dark web intelligence
- Gap analysis and threat modeling
- Remediation planning and execution support
Helping Your Defense Against Modern Threats
Continually strengthen your security to stay ahead of evolving threats.
Staying Aligned with our Clients
Reduce business risk while ensuring you’re always in control
- Executive and compliance oversight
- Program leadership and service improvements
- Sensitive hunts, investigations, and response
- Architecture and design authority
- Advisory and consultancy
Trust the Experts with Operational Expertise
Reduce your security operations workload with a comprehensive managed services solution.
- Threat intelligence and threat hunting
- Threat analysis and response services
- Security incident coordination
- Incident response services
- Platform engineering and management
- Identity and access management
- Content engineering and automation
- Vulnerability and remediation
Our Unique Accelerators
AI powered assets and digital workers throughout the threat lifecycle.
Automated security incident response, automated UEBA response (password change/MFA reset/etc.) accelerates response time by over 100%, significantly reducing the risk of compromise and preventing MFA-related breaches.
With over 200+ Unique indicators of compromise derived from years of experience in the security industry, our toolset stands apart from others in the industry.

Understanding the balance between function and security, especially in the medical industry, is key to our approach.
Tools & Technology
Maximizing investments for improved visibility & protection across a hybrid landscape.
Our Integrated Security Operating Model
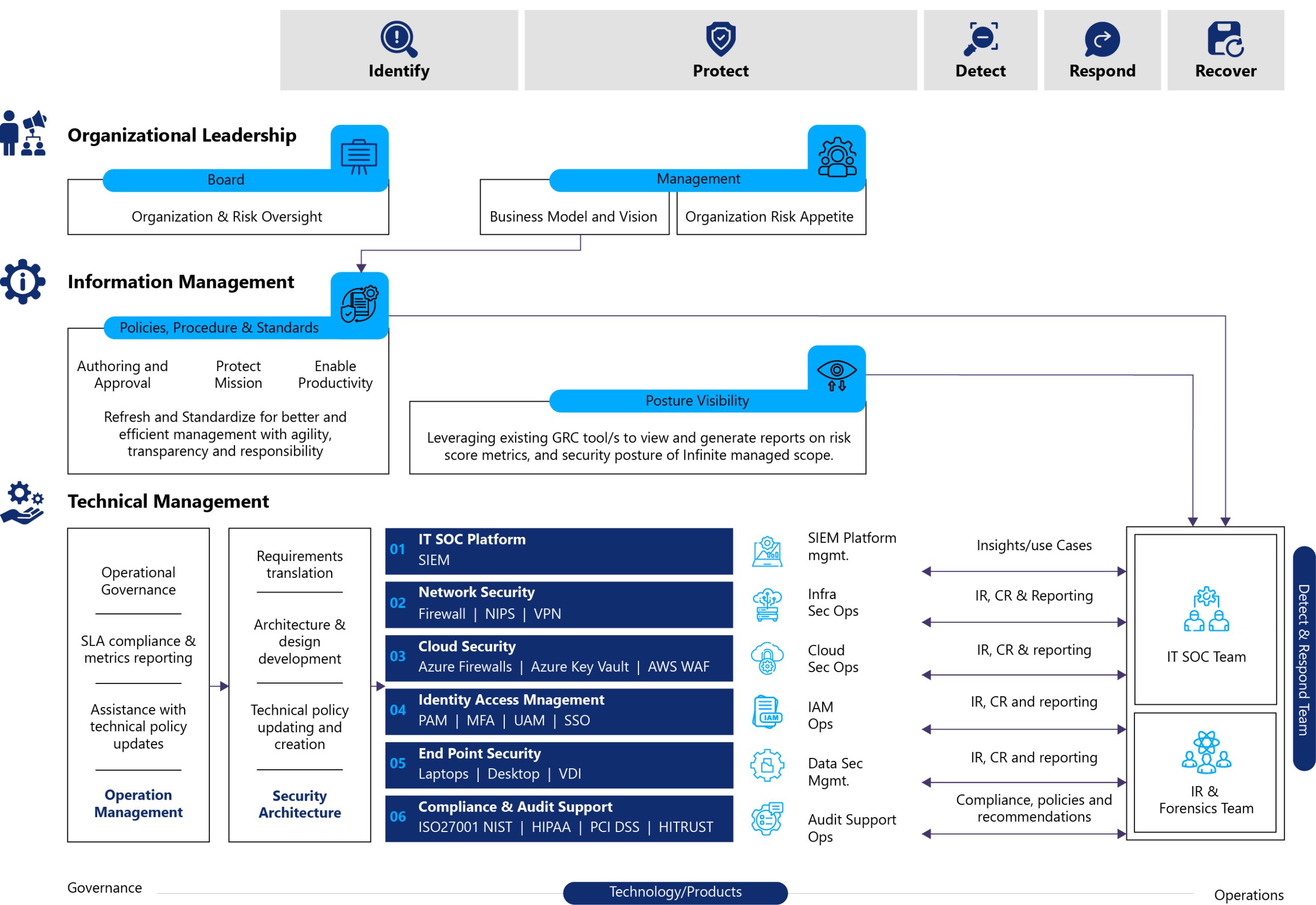
Challenges & Solutions
24/7 security operations with scalable support and intelligent triaging
Continuous vulnerability scanning and prioritized remediation strategy

















